The Local-Only Roadmap
The Local-Only Roadmap is your guide to private, cloud-free mobile apps. Whether you're validating an idea or ready to launch, this three-step process will help you rethink architecture from the ground up, starting with the user's device.
💡 Innovation Through Constraint
Before the Internet, all software was Local-Only by default. With the invention of the Internet and cloud-based computing, there was a significant shift to storing data in the cloud and the invention of real-time, anywhere collaboration. By embracing a new generation of Local-Only design principles, we can reinvent what it means to deliver privacy-focused, resilient, and collaborative mobile apps.
1. Evaluate: Is Your App a Local-Only Candidate?
Core Questions:
-
Does your app primarily manage personal user data that would benefit from enhanced privacy and user control on a mobile device?
Trade-off: Users gain control but give up automatic cross-device sync. -
Could your app's core functionality work without constant internet connectivity?
Trade-off: All core workflows must work completely offline. -
Does your app support occasional, proximity-based collaboration rather than continuous remote collaboration?
Trade-off: Local-Only apps using P2P connections work best when users can be physically near each other (using Bluetooth or local WiFi) and don't need constant synchronization across distances. Collaboration is possible, but it typically happens when users actively engage with their devices during real-time sessions. -
Would eliminating user accounts and cloud data storage simplify your app's development?
Trade-off: You'll need alternative strategies for user identification, content sharing, and device transitions.
What this means in practice:
-
Does your app need to pull data from external services to the mobile device, even if it stores and processes everything locally afterward?
Trade-off: A Local-Only app can fetch data from external APIs as long as that data is not stored in the cloud or sent to third-party services. Once retrieved, the data stays on the user's device or is shared intentionally over peer-to-peer connections that the user initiates. This approach allows for cloud-assisted input without cloud dependency, maintaining user control and enabling offline-first architecture once data is retrieved. -
Can your business model work without continuous user data access?
Trade-off: Usage analytics, improvement metrics, and behavior tracking will be significantly limited. -
Is your target audience technically savvy or privacy-conscious?
Trade-off: Local-Only apps appeal most strongly to users who value control and privacy over convenience. -
Are you comfortable implementing alternative mobile backup solutions?
Trade-off: Without the cloud, you must design explicit backup/restore mechanisms (e.g., exportable archives, device-to-device transfers).
2. Core Architecture Decisions
Local-Only apps have unique architecture requirements, including ensuring personal data is locally secure, using peer-to-peer technology for device-to-device communication, and building collaborative session management.
Local-Only Architecture: Data Flow
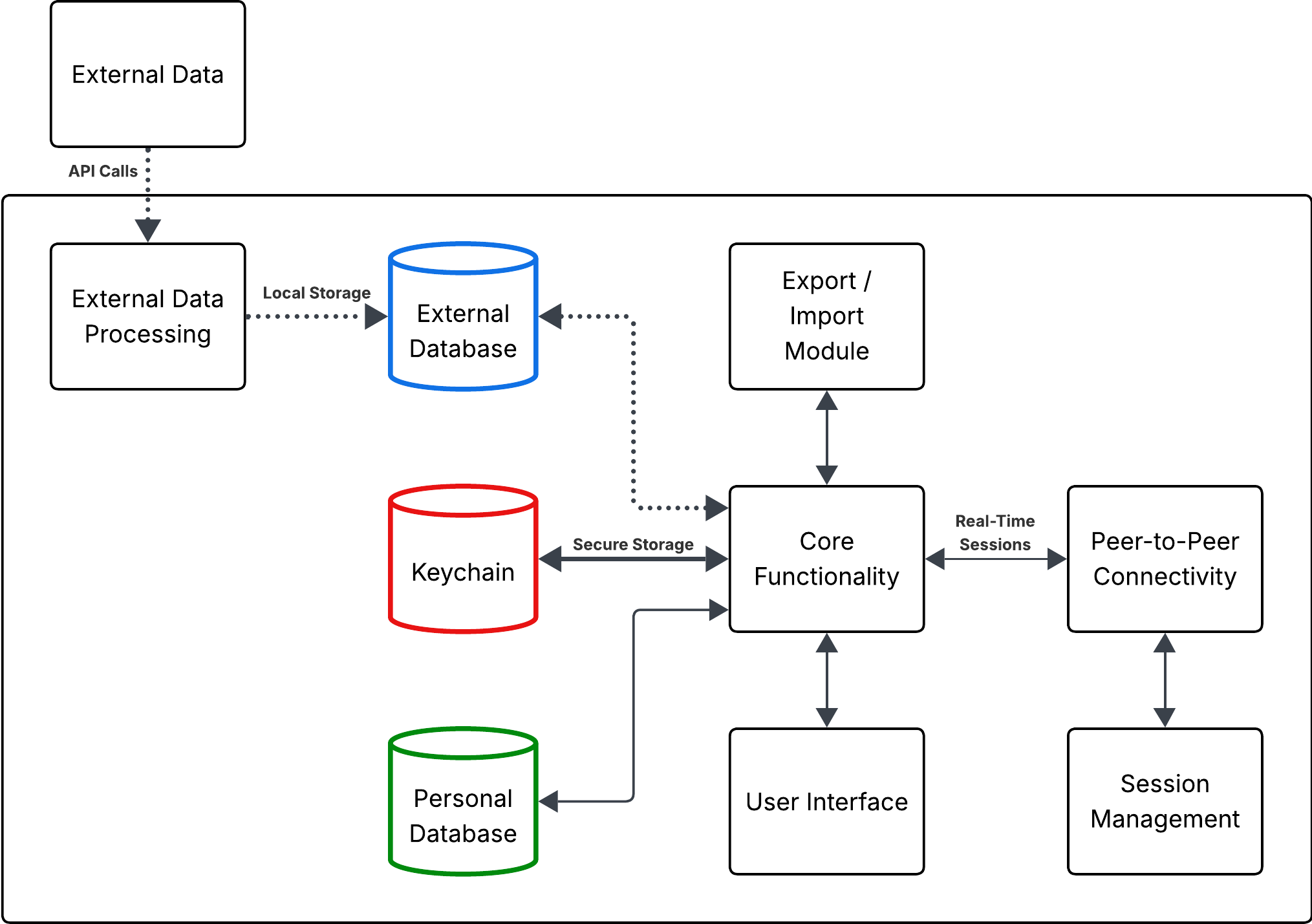
This diagram illustrates how cloud-assisted input can be processed locally and integrated with core functionality while maintaining Local-Only principles.
Data Classifications
There are three categories of data to be concerned about: secrets, personal data, and external data.
- Secrets data: device UUIDs, API keys, encryption keys
- Personal data: user preferences, watchlists, analysis results
- External data: movie metadata, financial account balances, recipe details
The app should store secret data, such as device IDs and encryption keys, in the Keychain and personal data supporting core functionality in a local database on the device. The app should logically or physically separate external data from personal data in a local database. Separating personal and external data will allow your app to independently secure, back up, or export each classification.
Device Identity
When your app needs to connect with one or more peer-to-peer devices, you will need a way to identify each device (peer). Without a login, your app lacks a username, email address, or database ID to determine who uses the mobile app. Generating a unique ID, such as a UUID, and storing it in the Keychain or a personal database provides your app with the unique identifier it needs for peer-to-peer collaboration.
You may not need a unique ID if your app doesn't have collaborative features, or you may want to maintain the identity to survive app installs and keep collaborative relationships intact.
External Data Integration
Your app may require external data, such as recipes, airline flight information, or access to streaming movies. Access to external data sources might require credentials, which must be stored as secret data.
Local-Only apps provide core functionality that can leverage external data to create personal value; however, the app's core intention should not solely display external data as is. For this reason, external data should be considered ephemeral and, in most cases, re-creatable by retrieving it from the external data source. Losing external data should be inconvenient, not catastrophic to the core functionality.
Treating external data as ephemeral reduces the need to back it up, moving the complexity from export/import to re-retrieving external data from the source.
Privacy and Security Model
Each app must define its security requirements based on the personal data it collects, explicitly considering the sensitivity and classifications of that data. A note-taking app has different privacy needs compared to a financial app.
Consider encryption for data storage and transport over peer-to-peer communication channels. Just because personal data is encrypted doesn't mean it should be shared with peers unless it is essential to the task and supports a core functionality.
While Local-Only apps do not require logins and the data is secure on the device, the app should implement controls to prevent anyone with access to the device from accessing the personal data in the app, using biometric or PIN authentication as a security measure.
Collaboration
Every Local-Only app has its collaboration model — how users connect, communicate, and share data without the cloud. In traditional apps, this logic lives on a server. However, in Local-Only architecture, the orchestration of collaboration moves into the app itself. From session management to data exchange, what used to be backend infrastructure now becomes part of the local user experience.
For example, in a collaborative note-taking app, the sharing scope might include document content but exclude user preferences; the sharing timeframe could be session-based for real-time editing; the sharing modes might allow read-only vs. edit permissions; and the Unique UX could show live cursors or typing indicators from peer devices.
Key use cases for collaboration:
- Sharing scope: Which data is shared vs. stays private on the device?
- Sharing timeframe: Is collaboration session-based or long-term?
- Sharing modes: What permission models govern access and visibility?
- Unique UX: How does the peer device reflect a shared state or intent?
State Machines
State machines provide structure and predictability when managing the complex, asynchronous workflows common in Local-Only apps.
Key use cases for state machines:
- Bluetooth Connection Management:
Handle the multi-step process of device discovery (advertising → services → characteristics → connected → ready) with clear state transitions and error handling - Peer-to-Peer Session Management:
Manage connection states (discovering → connecting → authenticating → collaborating → disconnecting) with proper cleanup and recovery - UI State Management:
Drive interface changes based on data availability, connection status, and user permissions (loading → ready → error → retry) - Asynchronous Workflows:
Handle request-response patterns like sending messages to peers and waiting for acknowledgments or data exchanges - Data Synchronization States:
Manage the flow of data sharing between devices (preparing → sending → confirming → complete) with rollback capabilities - Authentication and Security States:
Handle device identity verification and encryption key exchange workflows in P2P scenarios
Self-Healing
Two interesting challenges with Local-Only apps are limited insight into data integrity issues and access to app crash reports.
Unlike a cloud-based app, where all data is stored centrally in the cloud, a Local-Only app stores data locally on the device. You must find ways to identify and correct any data integrity issues and, if necessary, bring them to the user's attention so they can decide what to do next. Implement regular data integrity checks during app startup and after P2P data exchanges to catch corruption early. This proactiveness will reduce customer complaints and create a better customer experience.
To protect privacy, Local-Only apps should not automatically send crash reports to a central server, unlike cloud-based apps, which do this frequently. Options for managing crash reports in a privacy-centric manner are to capture them locally and ask the user to send them via email or allow uploads from the app to a central server only after obtaining explicit permission. Crash reports should never include personal data.
3. Build & Launch
Once your architecture is in place, it's time to implement your Local-Only app. This phase is where theory meets execution, from choosing a local database to handling peer-to-peer messaging protocols.
We're working on detailed guides, code examples, and component walkthroughs for Local-Only app development. Until then, explore our architecture in the article Reimagining Mobile App Architecture.